So, you’ve got a new cloud Ubuntu VPS & need to access it remotely?
The good news is that at Farbyte, SSH is enabled on our template-based cloud VPS by default!
If you install Ubuntu from ISO, instead of using a Ubuntu template on our Cloud KVM service, you can choose to also add an SSH server during the OS installation process.
This tutorial will show you how to enable OpenSSH on any Ubuntu 18.04 & 20.04 installation.
Both of these are Long Term Support (LTS) versions of Ubuntu & are thus great for running as servers.
All the administrative commands in this article assume you’re logged into the Ubuntu server as a user with sudo access.
Why Do I Need SSH On My Ubuntu Server?
If you’re not familiar with SSH, it stands for Secure Shell.
It allows you to make a remote connection to your Ubuntu server, or any other Linux server for that matter, via a very secure & encrypted connection.
Most Linux-based servers, like Ubuntu Server, don’t usually run a graphical user interface (GUI) like Windows.
For this reason, all administration is done via the command line, which is a bit like Microsoft DOS but much more powerful.
Check If SSH Is Already Running
It’s not unusual to already have SSH running on a Linux server, as it’s by far the most popular way of connecting to a remote server.
You can quickly check if your Ubuntu server is already running SSH by running the following command in a console or terminal window:
ps aux | grep sshIf SSH is already running on your server, you’ll usually see a few lines of output similar with one of them similar to:
root 744 0.0 0.5 69956 5456 ? Ss Mar06 0:00 /usr/sbin/sshd -DThe above line shows that the SSH daemon (server service) is running on the server already from /usr/sbin/sshd.
Another way to quickly check if SSH is already running is to run the following command:
netstat -napt | grep sshAgain, the above command may give you multiple lines of output, but the important line will look similar to:
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 744/sshdThe above line tells us that the SSH daemon is running in a listening state on port 22.
Port 22 is the standard SSH listening port & for security reasons should be changed for any Ubuntu server that is connected to the internet.
Install SSH Server
So, if you check for SSH using the above command & find that it’s not running the next step is to either login to the Ubuntu console, or open a terminal if you’re using a windows environment on your Ubuntu server.
OpenSSH is by far the most popular SSH server available for Linux & is completely free for personal or commercial use.
You can install it with the following command:
sudo apt install -y openssh-serverThis will install the SSH service on your Ubuntu server.
To make sure the SSH service is configured to start during system boot run the following command:
sudo systemctl enable sshd.serviceTo make sure the SSH service is running now, use the following command:
sudo systemctl start sshd.serviceTo check the current status of the SSH service run:
sudo systemctl start sshd.serviceBasic Ubuntu SSH Configuration
We find nano to be the easiest editor for working with Linux config files in the console.
To make sure you’ve got nano installed, run the following command:
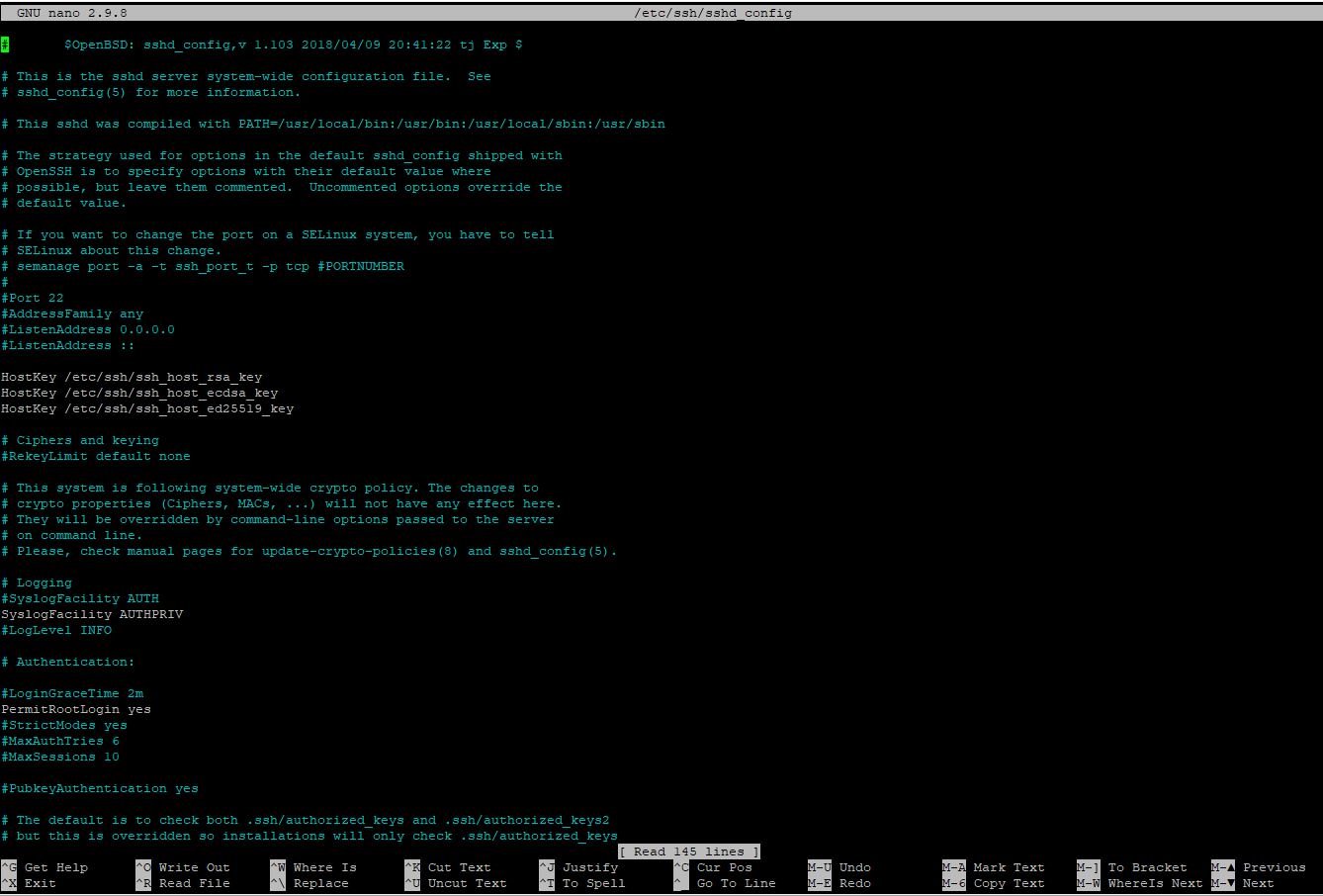
sudo apt install -y nanoAll the SSH service configurations can be changed by editing the /etc/ssh/sshd_config file.
You can open this for editing with nano as such:
sudo nano /etc/ssh/sshd_configSome common settings that Ubuntu administrators usually change are:
- Port – the port number the SSH service (daemon) listens on
- PermitRootLogin – whether to allow root to login via SSH
- PasswordAuthentication – whether to allow password-based authentication
- UseDNS – whether to perform a reverse DNS lookup on the connecting IP
There are many more server-side configuration options for OpenSSH.
To see a detailed explanation of each setting you can run the following command in your Ubuntu console:
man sshd_configAlternatively, you can read the sshd_config manual online.
Once you’ve made your changes to the SSH configuration file, you’ll need to restart the service:
sudo systemctl restart sshd.serviceIf you’ve got Uncomplicated Firewall (UFW) running on your Ubuntu server, you’ll need to open the SSH port in the firewall.
This can be done by running:
sudo ufw allow 22If you changed the default port number in your SSH config setting, you’ll need to replace 22 with that port number.
SSH Security Options
SSH is a very useful & powerful tool.
It allows you to remotely connect to your server from anywhere in the world.
Unfortunately, because of this, it’s also a primary target for hackers.
Here are 4 tips that will help secure your Ubuntu SSH service:
- Change to a non-default port number.
- Require certificate authentication.
- Limit access via a firewall.
- VPN SSH access.
1 – Change To A Non-Default Port Number
The first thing we recommend when enabling SSH is to change the listening port from the default 22 to something else, much higher up the port range.
Choose any port number between 1024 & 65535 & you should be OK.
This is security by obscurity & thus is only the first step in securing your SSH service.
It helps to keep your server off the radar of 1000’s of bots running on the internet checking port 22 every day!
This can be done by editing the SSH config file, which is normally located at /etc/ssh/sshd_config, with the following command:
sudo nano /etc/ssh/sshd_configOnce the file is open find the Port setting.
It will often be commented out with the # sign at the beginning of the line.
If so remove the comment & change the port to something you have selected.
#Port 22Exit nano (Ctrl+x) saving your changes & then restart the SSH service:
sudo systemctl restart sshd2 – Require Certificate Authentication
Now we’re really getting into the area of making your Ubuntu server SSH secure.
Configuring your SSH service to require SSH certificates from users that are logging in is an excellent way of improving the security of SSH.
It works by asking the connecting user for a certificate prior to allowing them to enter a password.
If the user doesn’t have the correct certificate for the user account they are trying to connect with, then they never get the opportunity to even enter a password.
Setting up the certificate & configuring SSH can seem overwhelming at first, but it’s well worth the effort.
3 – Limit Access Via A Firewall
Limiting access to the SSH service using a firewall can be simple, or quite complex depending on the firewall you’re using.
Limiting access will be dependant on blocking all access to your chosen SSH port based on the IP address of the connecting device.
For example, block all access except for IP address x.x.x.x.
This can be difficult if the remote users IP address changes frequently, as is often the case for residential & mobile connections.
Some firewalls, like pfSense, OPNsense, etc. allow you to specify hostnames in firewall rules, which they automatically & periodically update with the corresponding IP address.
This does, however, mean that you’ll need to also set up Dynamic DNS (DDNS) for the device or user hostname & ensure it is regularly updated (e.g. every 5 minutes or so).
4 – VPN SSH Access
This is probably the most secure method for setting up SSH on a Ubuntu server.
The idea is to not expose the SSH service to the internet, but instead only expose it to traffic that is connected to your virtual private network (VPN) network.
Ideally, you’d also implement some or all of the previously mentioned security tips.
For public-facing servers (e.g. web, email, etc.) using a VPN connection is the best solution for securing SSH access to your Ubuntu server.
Conclusion
Installing an SSH service on your Ubuntu VPS is a worthwhile & straightforward task.
In many cases, Ubuntu will come installed with an SSH service running by default.
SSH allows you to remotely administer your server from anywhere in the world.
However, with this improved convenience comes increased security threats
Security needs to be considered & measures put in place to restrict access to the SSH service (daemon) running on your Ubuntu server.